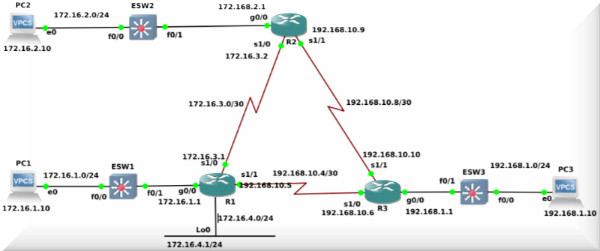
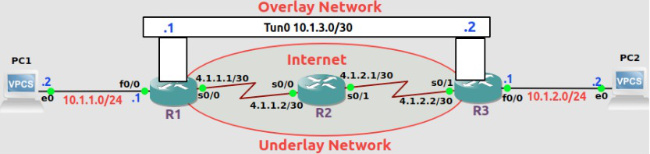
Since Generic Routing Encapsulation (GRE) VPN tunnels continue to remain on Cisco exams like CCNA and CCNP ENCOR, let’s demonstrate a quick configuration of a GRE tunnel.
Why do we care about GRE?
We care about GRE because it can encapsulate diverse network layer protocols that can be transported over an IP network between two locations over a public network like the Internet.
GRE can be used with or for:
* Multicast packets, such as OSPF, EIGRP, and streaming applications
* Connecting IPv6 networks over IPv4 networks
For purposes of this demonstration, we used the GNS3 emulation software running on a Linux VM.
The biggest problem with default GRE configuration (like the one below) is that it does not include security.
! Configure PC1
ip 10.1.1.2/24 10.1.1.1
save
! Configure PC2
ip 10.1.2.2/24 10.1.2.1
save
! Configure Router R1
conf t
hostname R1
interface f0/0
ip address 10.1.1.1 255.255.255.0
no shut
interface s0/0
ip address 4.1.1.1 255.255.255.252
no shut
! Configure Router R2
conf t
hostname R2
interface s0/1
ip address 4.1.1.2 255.255.255.252
no shut
int s0/0
ip address 4.1.2.1 255.255.255.252
no shut
! Configure Router R3
conf t
hostname R3
interface s0/1
ip address 4.1.2.2 255.255.255.252
no shut
interface f0/0
ip address 10.1.2.1 255.255.255.0
no shut
Static Routing
We’ll use static routing for end-to-end connectivity.
! Configure Static Routing on R1 & R3
!R1
conf t
ip route 0.0.0.0 0.0.0.0 4.1.1.2
!R3
conf t
ip route 0.0.0.0 0.0.0.0 4.1.2.1
GRE Tunnel Interfaces
Now it’s time to configure the GRE tunnel.
! Configure GRE Tunnel on R1
conf t
int tun 0
ip address 10.1.3.1 255.255.255.252
tunnel mode gre ip
tunnel source s0/0
tunnel destination 4.1.2.2
! Configure GRE Tunnel on R3
conf t
int tun 0
ip address 10.1.3.2 255.255.255.252
tunnel mode gre ip
tunnel source s0/1
tunnel destination 4.1.1.1
Let’s check the Tunnel Interfaces on R1 and R3 to make sure they’re up.
Verify Tunnel Interfaces
R1#sh ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.1.1.1 YES NVRAM up up
Serial0/0 4.1.1.1 YES NVRAM up up
FastEthernet0/1 unassigned YES NVRAM administratively down down
Serial0/1 unassigned YES NVRAM administratively down down
Serial0/2 unassigned YES NVRAM administratively down down
Serial0/3 unassigned YES NVRAM administratively down down
FastEthernet1/0 unassigned YES NVRAM administratively down down
FastEthernet2/0 unassigned YES NVRAM administratively down down
Tunnel0 10.1.3.1 YES NVRAM up up
R3#sh ip int br
Interface IP-Address OK? Method Status Protocol
FastEthernet0/0 10.1.2.1 YES NVRAM up up
Serial0/0 unassigned YES NVRAM administratively down down
FastEthernet0/1 unassigned YES NVRAM administratively down down
Serial0/1 4.1.2.2 YES NVRAM up up
Serial0/2 unassigned YES NVRAM administratively down down
Serial0/3 unassigned YES NVRAM administratively down down
FastEthernet1/0 unassigned YES NVRAM administratively down down
FastEthernet2/0 unassigned YES NVRAM administratively down down
Tunnel0 10.1.3.2 YES NVRAM up up
R3#
Configure EIGRP Routing on Tunnel Interfaces R1 and R3
! R1
conf t
router eigrp 100
network 10.0.0.0
no auto-summary
! R3
conf t
router eigrp 100
network 10.0.0.0
no auto-summary
Verify Routing on R1 and R3
R1#sh ip route
Codes: C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route
Gateway of last resort is 4.1.1.2 to network 0.0.0.0
4.0.0.0/30 is subnetted, 1 subnets
C 4.1.1.0 is directly connected, Serial0/0
10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
C 10.1.3.0/30 is directly connected, Tunnel0
D 10.1.2.0/24 [90/297270016] via 10.1.3.2, 00:21:00, Tunnel0
C 10.1.1.0/24 is directly connected, FastEthernet0/0
S* 0.0.0.0/0 [1/0] via 4.1.1.2
R1#
R3#sh ip route
Codes: C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route
Gateway of last resort is 4.1.2.1 to network 0.0.0.0
4.0.0.0/30 is subnetted, 1 subnets
C 4.1.2.0 is directly connected, Serial0/1
10.0.0.0/8 is variably subnetted, 3 subnets, 2 masks
C 10.1.3.0/30 is directly connected, Tunnel0
C 10.1.2.0/24 is directly connected, FastEthernet0/0
D 10.1.1.0/24 [90/297270016] via 10.1.3.1, 00:21:28, Tunnel0
S* 0.0.0.0/0 [1/0] via 4.1.2.1
R3#
Verify GRE
Now that we have configured the GRE VPN tunnel, let’s run some Verify commands on Routers R1 and R3.
We’ll start by verifying the tunnel0 interface on R1.
R1#show interface tunnel0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 10.1.3.1/30
MTU 1514 bytes, BW 9 Kbit/sec, DLY 500000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 4.1.1.1 (Serial0/0), destination 4.1.2.2
Tunnel protocol/transport GRE/IP
Key disabled, sequencing disabled
Checksumming of packets disabled
Tunnel TTL 255
Fast tunneling enabled
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Last input 00:00:03, output 00:00:01, output hang never
Last clearing of “show interface” counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
302 packets input, 25344 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
302 packets output, 25364 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
R1#
Let’s check the tunnel interface on router R3 now.
R3#show interface tunnel0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 10.1.3.2/30
MTU 1514 bytes, BW 9 Kbit/sec, DLY 500000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel source 4.1.2.2 (Serial0/1), destination 4.1.1.1
Tunnel protocol/transport GRE/IP
Key disabled, sequencing disabled
Checksumming of packets disabled
Tunnel TTL 255
Fast tunneling enabled
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Last input 00:00:03, output 00:00:04, output hang never
Last clearing of “show interface” counters never
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
316 packets input, 26540 bytes, 0 no buffer
Received 0 broadcasts, 0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
318 packets output, 26688 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
We can verify that the GRE tunnel is working fine by running traceroute on R1 and R3.
R1#traceroute 10.1.2.1
Type escape sequence to abort.
Tracing the route to 10.1.2.1
1 10.1.3.2 8 msec 0 msec 0 msec
We can see that the packet is moving through the tunnel interface.
R3#traceroute 10.1.1.1
Type escape sequence to abort.
Tracing the route to 10.1.1.1
1 10.1.3.1 4 msec 4 msec 0 msec
Troubleshooting GRE
* Tunnel Interface IP addresses on either side must be in same subnet
* Subnet masks on both sides of the tunnel must match
* Check if interfaces for tunnel source/destination are configured with correct IP address
* Check if Tunnel interfaces are up
* Verify if static or dynamic routing is configured properly
Adding Security to GRE via IPSec
The biggest drawback of GRE is that GRE by itself does not provide security.
So we leverage IPSec to strengthen GRE.
In a following blog post, we’ll demonstrate GRE with IPSec.