Let’s admit the truth, shall we.
Even the best of us command line gurus (and only few of us are really gurus) prefer the simplicity and ease of a GUI frontend to our favorite command line tools.
Zenmap is a neat GUI tool for the nmap command line scanning utility found in the Kali Linux penetration test distribution.
For sure, nmap is a great scanning tool but newbies may find it intimidating considering the hundreds of options the command line utility has.
That’s where Zenmap comes in.
For newcomers to nmap who can’t be bothered to learn the command line syntax or beginners struggling with the nmap syntax, Zenmap is like unexpectedly finding a pot of gold.
Life can’t get better! 😉
As far as I can tell, Zenmap comes along with nmap in Kali Linux.
But when I installed nmap on an Ubunutu/LinuxMint desktop and later on a CentOS 7 system, I noticed that Zenmap did not accompany nmap in both instances. I had to do a separate install on the LinuxMint system.
$ apt-get install zenmap
I was surprised to not find Zenmap in the base CentOS repositories (but nmap is there).
How to Use Zenmap
The great beauty of Zenmap is that it lets you hit the ground running.
All it takes is a few seconds to get the program up, pick your options and get going.
Type zenmap on the command line and the GUI frontend opens up.
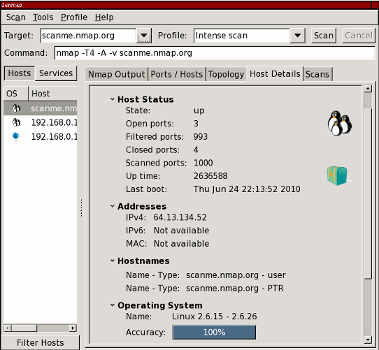
Enter the host name (a domain or IP address) you wish to scan and in the drop-down box to the right, select the type of scan you want to run.
That’s all you need to do to scan for vulnerabilities on a host.
A huge plus is that the tool displays the command line syntax for the profile you pick. I consider it a nice way to let beginners pick up the command line syntax for nmap.
Different Zenmap Scans
There are scans of various degrees of complexity and duration that you can run on Zenmap.
You can pick from ping, quick scan, ping scan, intense scan, quick scan plus, slow comprehensive scan and more types. Continue reading »



 These days online attacks on your server and/or your web site can come from any corner of the world.
These days online attacks on your server and/or your web site can come from any corner of the world.