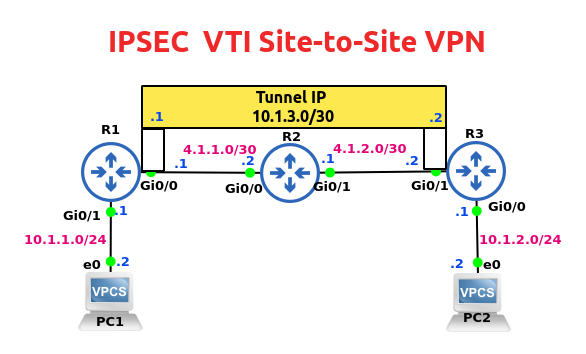
Let’s configure a VTI site-to-site Virtual Private Network in this lab.
In this VPN lab, we’re running IPSEC as the native protocol on the tunnel interface.
We’re not using Generic Routing Encapsulation (GRE) in this VPN lab.
The lab will also demonstrate use of a dynamic routing protocol (EIGRP) between routers R1 and R3 on the Tunnel interface and for the two LAN segments.
So obviously we’ll also be using Multicast over the tunnel interface.
After the IPSEC VPN is configured, we’ll run a bunch of show/verify commands.
Why VTI?
So why would we want to use static VTI/IPsec to create a site-to-site VPN instead of the GRE/IPsec option or the older cryptomap/ACL based VPN?
For one, the GRE header adds an extra 4-bytes. So avoiding GRE eliminates that bandwidth overhead.
Also, unlike with the cryptomap/ACL based VPN option in the static VPN model the IPsec tunnel is “on” all the time.
VTI’s support for QoS and multicast (just like with GRE/IPsec) means we can use dynamic routing protocols here.
Then there’s the issue of scalability. Some networking experts consider VTI more scalable than GRE/IPsec but if you ask me the scalability issue in larger networks is better addressed with Dynamic Multipoint Virtual Private Networks (DMVPN).
This lab is running on the GNS3 network simulation tool.
Configurations
IP addresses of the end-devices on the LAN segment and of the three routers have already been configured.
You can check them by viewing the topology diagram at the top of this post.
We’ll start with static routing to ensure end-end connectivity from R1 to R3.
Configure Static Routing on R1 & R2
R1
conf t
ip route 0.0.0.0 0.0.0.0 4.1.1.2
end
R3
conf t
ip route 0.0.0.0 0.0.0.0 4.1.2.1
end
VTI IPsec Configuration
Now it’s time for the meat of this lab, the VTI IPSec configuration to build the Virtual Private Network (VPN).
R1 VTI Configuration
IKE Phase 1
*********************
Set Global IKE policy
Configure Phase 1 Tunnel (ISAKMP Parameters)
conf t
crypto isakmp policy 10
encryption aes 256
hash sha256
authentication pre-share
group 16
lifetime 3600
crypto isakmp key Cisco123 address 4.1.2.2
Configure Phase 2 Tunnel on R1
crypto ipsec transform-set BTS esp-aes 256 esp-sha256-hmac
mode tunnel
crypto ipsec profile JULY-2022-PROFILE
set transform-set BTS
exit
! Configure Tunnel Interface
int tun 0
ip address 10.1.3.1 255.255.255.252
tunnel source g0/0
tunnel destination 4.1.2.2
tunnel mode ipsec ipv4
tunnel protection ipsec profile JULY-2022-PROFILE
qos pre-classify
end
Note: The tunnel mode ipsec ipv4 command is not used in GRE/IPsec VPN.
Having completed the IPSec configuration for R1, we’re ready to configure R3.
Except for the lifetime configuration, the other parameters in the Phase 1 Tunnel should match on R1 and R3 routers.
R3 VTI Configuration
*********************
Configure Phase 1 Tunnel
conf t
crypto isakmp policy 10
encryption aes 256
hash sha256
authentication pre-share
group 16
lifetime 3600
crypto isakmp key Cisco123 address 4.1.1.1
Configure Phase 2 Tunnel on R3
crypto ipsec transform-set BTS esp-aes 256 esp-sha256-hmac
mode tunnel
crypto ipsec profile JULY-2022-PROFILE
set transform-set BTS
exit
Configure Tunnel Interface
int tun 0
ip address 10.1.3.2 255.255.255.252
tunnel source g0/1
tunnel destination 4.1.1.1
tunnel mode ipsec ipv4
tunnel protection ipsec profile JULY-2022-PROFILE
qos pre-classify
end
===================================================================
EIGRP Protocol for Tunnel & LAN
Let’s set up a dynamic routing protocol for the LAN segments and for the tunnel.
We’ll use EIGRP this time.
R1
conf t
router eigrp 12
network 10.1.1.0 0.0.0.255
network 10.1.3.0 0.0.0.3
no auto-summary
end
R3
conf t
router eigrp 12
network 10.1.2.0 0.0.0.255
network 10.1.3.0 0.0.0.3
no auto-summary
end
===================================================================
Key IPSec Show Commands
There are a whole bunch of show or verify commands when it comes to a Site-to-Site VPN configuration.
sh run | s crypto
sh crypto isakmp policy
sh crypto isakmp key
sh crypto isakmp sa
sh int tun0
sh crypto ipsec profile
sh crypto ipsec transform-set
We’ll run them all below.
It’s always a good idea to check our IPSec configuration with show run | section crypto before we dive into other show commands.
This also gives us an opportunity to identify errors if any.
R1#sh run | section crypto
crypto isakmp policy 10
encr aes 256
hash sha256
authentication pre-share
group 16
lifetime 3600
crypto isakmp key Cisco123 address 4.1.2.2
crypto ipsec transform-set BTS esp-aes 256 esp-sha256-hmac
mode tunnel
crypto ipsec profile JULY-2022-PROFILE
set transform-set BTS
R1#
Before we launch into the other IPSec commands, let’s check the EIGRP routes.
Sure enough, the EIGRP routes are seen below.
Note that the LAN segment of R3 (10.1.2.0 network) is being accessed over the tunnel.
R1#sh ip route eigrp
Codes: L – local, C – connected, S – static, R – RIP, M – mobile, B – BGP
D – EIGRP, EX – EIGRP external, O – OSPF, IA – OSPF inter area
N1 – OSPF NSSA external type 1, N2 – OSPF NSSA external type 2
E1 – OSPF external type 1, E2 – OSPF external type 2
i – IS-IS, su – IS-IS summary, L1 – IS-IS level-1, L2 – IS-IS level-2
ia – IS-IS inter area, * – candidate default, U – per-user static route
o – ODR, P – periodic downloaded static route, H – NHRP, l – LISP
a – application route
+ – replicated route, % – next hop override, p – overrides from PfR
Gateway of last resort is 4.1.1.2 to network 0.0.0.0
10.0.0.0/8 is variably subnetted, 5 subnets, 3 masks
D 10.1.2.0/24 [90/26880256] via 10.1.3.2, 00:10:28, Tunnel0
Several Show Options
To get a better idea of the IPSec show commands, we’ve shown below the various options available with show crypto isakmp.
R1#sh crypto isakmp ?
default Show ISAKMP default
key Show ISAKMP preshared keys
peers Show ISAKMP peer structures
policy Show ISAKMP protection suite policy
profile Show ISAKMP profiles
sa Show ISAKMP Security Associations
Let’s pick show crypto isakmp policy as our next IPSec show command.
R1#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: AES – Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard 2 (256 bit)
authentication method: Pre-Shared Key
Diffie-Hellman group: #16 (4096 bit)
lifetime: 3600 seconds, no volume limit
R1#sh crypto isakmp key
Keyring Hostname/Address Preshared Key
default 4.1.2.2 Cisco123
===============
Packet Encryption & Decryption
We can view details of encryption and decryption with sh crypto ipsec sa | in encap|decap.
R1#sh crypto ipsec sa | in encap|decap
#pkts encaps: 9017, #pkts encrypt: 9017, #pkts digest: 9017
#pkts decaps: 9020, #pkts decrypt: 9020, #pkts verify: 9020
R1#sh crypto ipsec sa | in encap|decap
#pkts encaps: 9597, #pkts encrypt: 9597, #pkts digest: 9597
#pkts decaps: 9601, #pkts decrypt: 9601, #pkts verify: 9601
R1#sh crypto ipsec sa | in encap|decap
#pkts encaps: 9837, #pkts encrypt: 9837, #pkts digest: 9837
#pkts decaps: 9841, #pkts decrypt: 9841, #pkts verify: 9841
R1#sh crypto ipsec sa | in encap|decap
#pkts encaps: 10039, #pkts encrypt: 10039, #pkts digest: 10039
#pkts decaps: 10043, #pkts decrypt: 10043, #pkts verify: 10043
R1#sh crypto ipsec sa | in encap|decap
#pkts encaps: 10041, #pkts encrypt: 10041, #pkts digest: 10041
#pkts decaps: 10045, #pkts decrypt: 10045, #pkts verify: 10045
R1#
Let’s check the details of our tunnel interface on router R1.
R1#sh run int tun0
Building configuration…
Current configuration : 217 bytes
!
interface Tunnel0
ip address 10.1.3.1 255.255.255.252
qos pre-classify
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel destination 4.1.2.2
tunnel protection ipsec profile JULY-2022-PROFILE
R1#sh int tun0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 10.1.3.1/30
MTU 17878 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel linestate evaluation up
Tunnel source 4.1.1.1 (GigabitEthernet0/0), destination 4.1.2.2
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with GigabitEthernet0/0
Set of tunnels with source GigabitEthernet0/0, 1 member (includes iterators), on interface
Tunnel protocol/transport IPSEC/IP
Tunnel TTL 255
Tunnel transport MTU 1438 bytes
Tunnel transmit bandwidth 8000 (kbps)
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “JULY-2022-PROFILE”)
Last input never, output never, output hang never
Last clearing of “show interface” counters 00:01:33
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo (QOS pre-classification)
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
31 packets input, 2104 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
31 packets output, 2006 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
==================================================================
Verify IPsec Profile
R1#sh crypto ipsec profile
IPSEC profile JULY-2022-PROFILE
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Mixed-mode : Disabled
Transform sets={
BTS: { esp-256-aes esp-sha256-hmac } ,
}
IPSEC profile default
Security association lifetime: 4608000 kilobytes/3600 seconds
Responder-Only (Y/N): N
PFS (Y/N): N
Mixed-mode : Disabled
Transform sets={
default: { esp-aes esp-sha-hmac } ,
}
R1#
R1#sh crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
21 IPsec AES256+SHA256 0 548 548 4.1.1.1
22 IPsec AES256+SHA256 550 0 0 4.1.1.1
R1#
==================================================================
Verify Transform-Set
R3#sh crypto ipsec transform-set
Transform set default: { esp-aes esp-sha-hmac }
will negotiate = { Transport, },
Transform set BTS: { esp-256-aes esp-sha256-hmac }
will negotiate = { Tunnel, },
R3#sh crypto ipsec sa
interface: Tunnel0
Crypto map tag: Tunnel0-head-0, local addr 4.1.2.2
protected vrf: (none)
local ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
remote ident (addr/mask/prot/port): (0.0.0.0/0.0.0.0/0/0)
current_peer 4.1.1.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 206, #pkts encrypt: 206, #pkts digest: 206
#pkts decaps: 205, #pkts decrypt: 205, #pkts verify: 205
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 4.1.2.2, remote crypto endpt.: 4.1.1.1
plaintext mtu 1438, path mtu 1500, ip mtu 1500, ip mtu idb GigabitEthernet0/1
current outbound spi: 0x3C8F2A78(1016015480)
PFS (Y/N): N, DH group: none
inbound esp sas:
spi: 0xE35B4447(3814409287)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 1, flow_id: SW:1, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4608000/2718)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x1D165E9F(488005279)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 3, flow_id: SW:3, sibling_flags 80004040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4162768/2718)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
inbound ah sas:
inbound pcp sas:
outbound esp sas:
spi: 0x9E3A7B85(2654632837)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 2, flow_id: SW:2, sibling_flags 80000040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4608000/2718)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
spi: 0x3C8F2A78(1016015480)
transform: esp-256-aes esp-sha256-hmac ,
in use settings ={Tunnel, }
conn id: 4, flow_id: SW:4, sibling_flags 80004040, crypto map: Tunnel0-head-0
sa timing: remaining key lifetime (k/sec): (4162768/2718)
IV size: 16 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
outbound ah sas:
outbound pcp sas:
R3#
R3#sh crypto engine connections active
Crypto Engine Connections
ID Type Algorithm Encrypt Decrypt LastSeqN IP-Address
21 IPsec AES256+SHA256 0 634 634 4.1.2.2
22 IPsec AES256+SHA256 632 0 0 4.1.2.2
R3#
R3#sh ip int tun0
Tunnel0 is up, line protocol is up
Internet address is 10.1.3.2/30
Broadcast address is 255.255.255.255
Address determined by non-volatile memory
MTU is 1438 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.10
Outgoing access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is enabled
IP fast switching on the same interface is disabled
IP Flow switching is disabled
IP CEF switching is enabled
IP CEF switching turbo vector
IP Null turbo vector
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Policy routing is disabled
Network address translation is disabled
BGP Policy Mapping is disabled
Input features: MCI Check
Output features: QoS Preclassification
Post encapsulation features: IPSEC Post-encap output classification
IPv4 WCCP Redirect outbound is disabled
IPv4 WCCP Redirect inbound is disabled
IPv4 WCCP Redirect exclude is disabled
R3#
R3#sh int tun0
Tunnel0 is up, line protocol is up
Hardware is Tunnel
Internet address is 10.1.3.2/30
MTU 17878 bytes, BW 100 Kbit/sec, DLY 50000 usec,
reliability 255/255, txload 1/255, rxload 1/255
Encapsulation TUNNEL, loopback not set
Keepalive not set
Tunnel linestate evaluation up
Tunnel source 4.1.2.2 (GigabitEthernet0/1), destination 4.1.1.1
Tunnel Subblocks:
src-track:
Tunnel0 source tracking subblock associated with GigabitEthernet0/1
Set of tunnels with source GigabitEthernet0/1, 1 member (includes iterators), on interface
Tunnel protocol/transport IPSEC/IP
Tunnel TTL 255
Tunnel transport MTU 1438 bytes
Tunnel transmit bandwidth 8000 (kbps)show
Tunnel receive bandwidth 8000 (kbps)
Tunnel protection via IPSec (profile “JULY-2022-PROFILE”)
Last input never, output never, output hang never
Last clearing of “show interface” counters 00:17:56
Input queue: 0/75/0/0 (size/max/drops/flushes); Total output drops: 0
Queueing strategy: fifo (QOS pre-classification)
Output queue: 0/0 (size/max)
5 minute input rate 0 bits/sec, 0 packets/sec
5 minute output rate 0 bits/sec, 0 packets/sec
243 packets input, 14702 bytes, 0 no buffer
Received 0 broadcasts (0 IP multicasts)
0 runts, 0 giants, 0 throttles
0 input errors, 0 CRC, 0 frame, 0 overrun, 0 ignored, 0 abort
245 packets output, 15496 bytes, 0 underruns
0 output errors, 0 collisions, 0 interface resets
0 unknown protocol drops
0 output buffer failures, 0 output buffers swapped out
R3#
R3#sh crypto isakmp policy
Global IKE policy
Protection suite of priority 10
encryption algorithm: AES – Advanced Encryption Standard (256 bit keys).
hash algorithm: Secure Hash Standard 2 (256 bit)
authentication method: Pre-Shared Key
Diffie-Hellman group: #16 (4096 bit)
lifetime: 3600 seconds, no volume limit
===================
Testing End-to-End Connectivity
Let’s check end-to-end connecity now.
Can PC1 ping PC2?
And the answer is yes.
PC1> ping 10.1.2.2
84 bytes from 10.1.2.2 icmp_seq=1 ttl=62 time=9.873 ms
84 bytes from 10.1.2.2 icmp_seq=2 ttl=62 time=10.177 ms
84 bytes from 10.1.2.2 icmp_seq=3 ttl=62 time=10.509 ms
84 bytes from 10.1.2.2 icmp_seq=4 ttl=62 time=6.715 ms
84 bytes from 10.1.2.2 icmp_seq=5 ttl=62 time=11.206 m
What about traceroute?
Just like the ping ICMP protocol on which it relies, traceroute goes via the tunnel interface too.

Sorry, the comment form is closed at this time.